
What is Cross-site Scripting
Cross-site Scripting (X.S.S) is a client-side code injection attack.
The attacker aims to execute malicious scripts in a web browser rather then at the server side.These flaws can occur when the application takes not trusted data and send it to the web browser without proper validation.
Attackers can use X.S.S to execute malicious scripts on the users in this case victim browsers. Since the browser cannot know if the script is trusty or not, the script will be executed, and the attacker can hijack session cookies, deface websites, or redirect the user to an unwanted and malicious websites.
Implication
Making the use of this security vulnerability, an attacker can inject scripts into the application, can steal session cookies, deface websites, and can run malware on the victim’s Devices.
wiki help
script example
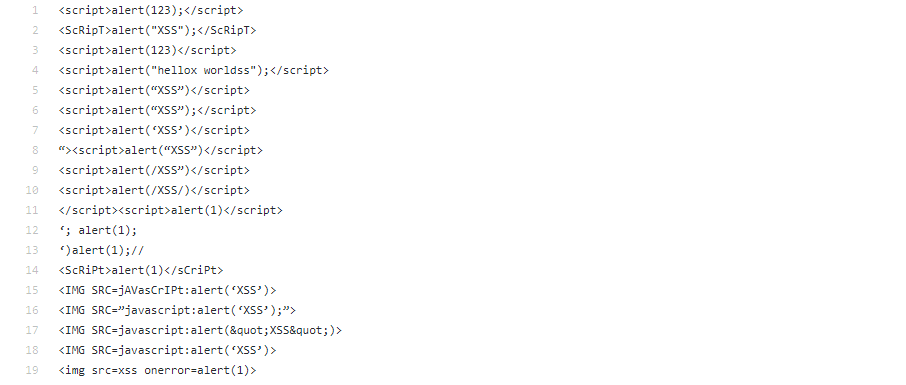
Vulnerable Objects
-Input Fields
-URLs
Examples
1.http://www.testsite.com/names/?query=<script>alert(“xss”)</script>
The above script when run on a browser, a message box will be displayed if the site is vulnerable to XSS
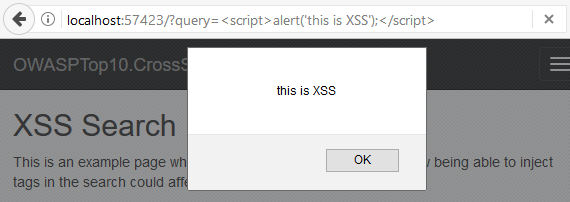
2.http://www.testsite.com/names/?query=<script>alert(document.cookie)</script>
The above script when run, the browser will alert containing site cookie.
The more serious attack can be done by running malicious scripts.
prevention
Validating Input
Input validation, also known as data validation, is the proper testing of any input supplied by a user or application. Input validation prevents improperly formed data from entering an information system. Because it is difficult to detect a malicious user who is trying to attack software, applications should check and validate all input entered into a system. Input validation should occur when data is received from an external party, especially if the data is from not trusted sources.
Input Output encoding
When processing intrusted user input for (web) applications, filter the input, and encode the output.Encoding is dependent on the type of output – which means that for example a string, which will be used in a JavaScript variable, should be treated (encoded) differently than a string which will be used in plain HTML.